Once the SSH server started, the bots will randomly try brute-force the SSH server, some servers need to keep using default port 22 for various reasons. The most reasonable reason is to whitelist the IP address of the users or use IPv6 which had less bot brute-forcing your server.
Another solution is using sshguard, sshguard is a daemon that protects SSH from brute-force.
Install sshguard
Install sshguard using apt package manager
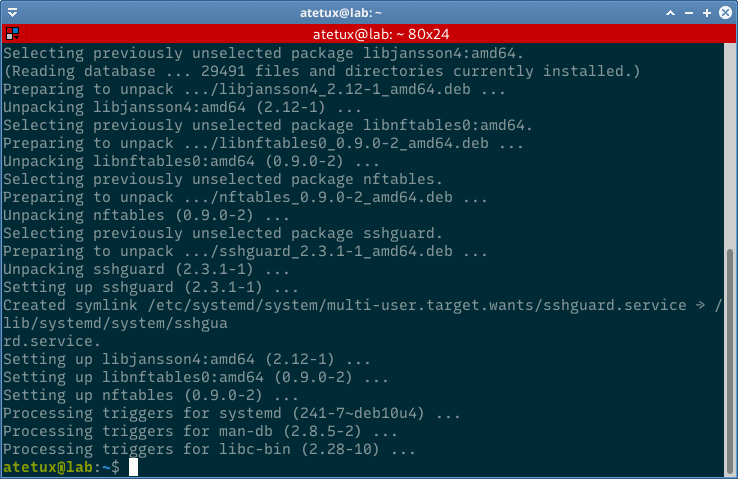
Few minutes after install sshguard, it already caught a few IP address
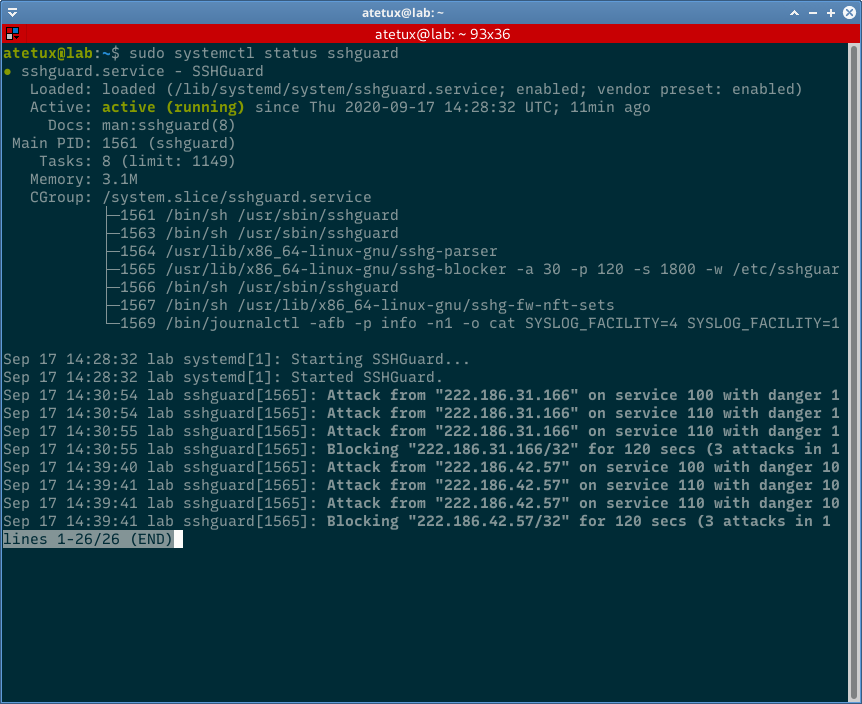
For the general server, the default sshguard already enough to protect their server, because Debian runs the service after the installation, no need to run the services or activate after reboot, the installation process already takes care of that.
sshguard Configuration
On Debian, sshguard can be found on /etc/sshguard/ directory especially the /etc/sshguard/sshguard.conf file, for my production server I usually only changes the BLOCK_TIME from 120 second to 86400 second (1 day). Use these one-liner to change the BLOCK_TIME value
sed -i "s/BLOCK_TIME=120/BLOCK_TIME=86400" /etc/sshguard/sshguard.conf
restart sshguard to apply changes
sudo systemctl restart sshdTesting sshguard
Use another server with different public IP from your computer to avoid locking.
To test brute-force our own SSH, install sshpass
sudo apt install sshpass -y
the run this simple scripts
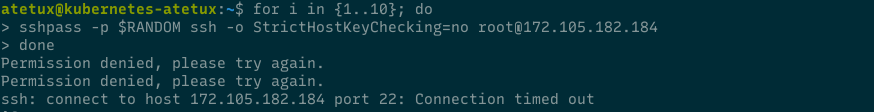
for i in {1..10}; do sshpass -p $RANDOM ssh -o StrictHostKeyChecking=no root@SERVER-IP done
script above will try to login to server 10 times with random password, of course it will failed. After the third failed attempt sshguard will block the IP address
on Server check the sshguard log, you’ll find the
sudo journalctl -u sshguard -f ... ... Sep 17 15:00:13 lab sshguard[1565]: Blocking "172.105.170.229/32" for 120 secs (3 attacks in 1 secs, after 1 abuses over 1 secs.) ... ...
Blacklist IP Address
To list the blacklisted IP Address, run sudo nft list set ip sshguard attackers
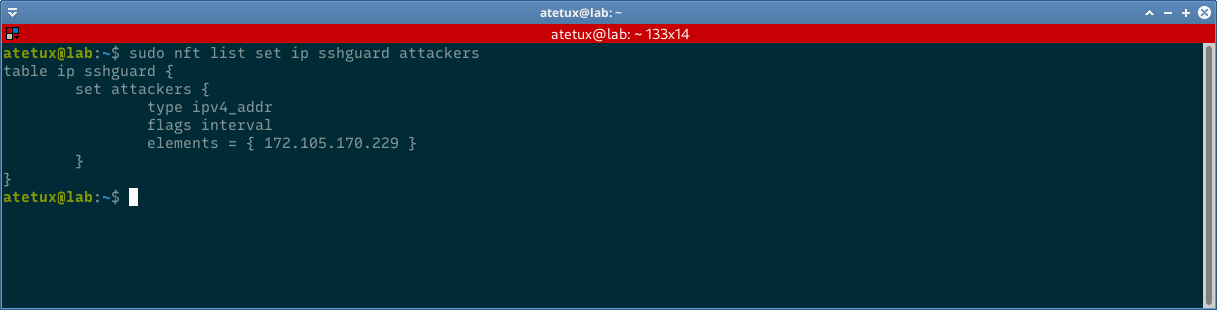
to unban the IP address (remove IP address from blacklist)
sudo nft delete element ip sshguard attackers { IPADDRESS }
Whitelist IP Address
Whitelist ip address to avoid banned by sshguard
sudo sshguard -w IP-ADDRESS
another way is to append IP Address on /etc/sshguard/whitelist
echo "IP-ADDRESS/32" | sudo tee -a /etc/sshguard/whitelist